QKD Becomes an Essential Part of Quantum Safety
The first Quantum Key Distribution (QKD) protocol was proposed in 1984, forming a very “cool” method to leverage the fundamental property of quantum nature that if you observe a system, you irreversibly change its properties. This is a fancy way of saying that this system is tamper proof. Any attempt to intercept the signal will inevitably leave a trace and hence be detected.
This property elevated QKD into the big blue sky of exaggeration, wild claims and sheer lies. Anyone who knows Gartner’s hype cycle shouldn’t be surprised as the claims got bigger and bigger on the way up the cycle.
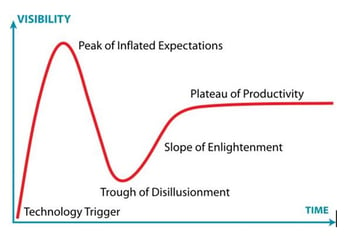
Unhackable, guaranteed by the laws of physics, … offers the ultimate security, … provides perfect security, … statements like these were all too common, and for hackers and security researchers they almost seemed like a call-to-action to dig into it. (“Peak of Inflated Expectations”).
The fundamental QKD method provides an information-theoretic security guarantee that you won’t find anywhere else and that is second to none. In case you are not familiar with this concept, information theoretic security means that the system is analytically unbreakable, i.e. it remains safe even against an attacker with unlimited computing power.
Of course, every implementation can have flaws. Microsoft issues a patch every month to fix issues in their products, so it is fair to say that QKD implementations will not be perfect either. Indeed, every classical encryption method used today also has this challenge and, more importantly, doesn’t have that all-important information-theoretic secure proof. This means that they are vulnerable not only to system flaws (DES, MD5, …), but also to advancements in computing power (e.g. Quantum Computers) that will break even a perfect implementation of RSA. For QKD the attack surface is vastly smaller since fundamental theory shows it to be information-theoretic secure.
Critics have mentioned among other things that QKD is not flexible enough, that it is inherently a point-to-point connection, that it is expensive (“Trough of Disillusionment”). They have certainly raised some valid issues at times, however newer implementations address almost all of these criticisms. Indeed, looking at the Gartner Hype Cycle, I feel that we are now on our way up the “Slope of Enlightenment”.
QKD is really emerging right now in many different conversations as the new weapon for protecting critical data moving along communication networks. From a practical implementation perspective, I was lucky enough to attend this week’s launch of UK’s Quantum Network segment between Adastral Park and Cambridge. BT is using QKD to exchange encryption keys between these two sites, which can now be used to provide the strongest possible security. QuintessenceLabs has played a big part of this launch by providing our Key Management products and expertise into the overall solution. Check the “Video Messaging Solution Secured by QKD” press release for more information.
BT’s managing director of research Tim Whitley said that “We’re proud to be at the forefront of the next generation of network design, helping the UK take the lead in the development of ultra-secure quantum networks, and keeping our customers’ data safe in years to come.”
At last week’s Inside Quantum Technology (IQT) conference “The Future of Quantum Computing and Quantum Cryptography”, attendees heard for two days that any Strategy to become “Quantum Safe” involves both Post-Quantum-Algorithms (PQA) and Quantum Key Distribution (QKD). It’s not one or the other, it’s a combination of both. That was the overwhelming message attendees heard from multiple speakers.
Seems like QKD is another technology that follows Gartner’s Hype Cycle and also that it has made it through the “Through of Disillusionment” and is now on the way to Productivity.
Now is the perfect time to explore where QKD would fit into your organization as part of your strategy to become Quantum Safe. QuintessenceLabs is working on the next-generation of QKD system where we can generate much, much higher key rates than current legacy systems, an essential characteristic for most real-world applications.
If you are interested or want more information, visit “Our Technology” page and please do get in touch. We’d love to hear from you.
Andreas Baumhof, Vice President of Quantum Technologie
Share this
You May Also Like
These Related Posts

A Quantum Safe World

Quantum Politics


